Munga Bunga`s Http Brute Force S
Often Web sites advise users to choose memorable passwords such as birthdays, names of friends or family, or social security numbers. This is extremely poor advice, as such passwords are easily guessed by an attacker who knows the user.
The most common way an attacker will try to obtain a password is through the dictionary attack’. In a dictionary attack, the attacker takes a dictionary of words and names, and tries each one to see if it is the require password. This can be automated with programs which can guess hundreds or thousands of words per second. This makes it easy for attackers to try variations: word backwards, different capitalization, adding a digit to the end, and popular passwords. Another well-known form of attack is the hybrid attack.

A hybrid attack will add numbers or symbols to the filename to successfully crack a password. Often people change their passwords by simply adding a number to the end of their current password. The pattern usually takes this form: first month password is “site”; second month password is “site2”; third month password is “site2”; and so on. A brute force attack is the most comprehensive form of attack, though it may often take a long time to work depending on the complexity of the password. Some brute force attacks can take a week depending on the complexity of the password. Webcracker allows the user to test a restricted-access website by testing id and password combinations on the web site.This program exploits a rather large hole in web site authentication methods.
Password protected websites may be easily brute-force hacked, if there is no set limit on the number of times an incorrect password or User ID can be tried.WebCracker is a simple tool that takes text lists of usernames and passwords and uses them as dictionaries to implement Basic authentication password guessing. Brutus does very weak target verification before starting; in fact all it does is connect to the target on the specified port.
In the context of Brutus, the target usually provides a service that allows a remote client to authenticate against the target using client supplied credentials. The user can define the form structure to Brutus of any given HTML form. This will include the various form fields, any cookies to be submitted in requests, the HTTP referrer field to send (if any) and of course the authentication response strings that Brutus uses to determine the outcome of an authentication attempt. If Brutus can successfully read forms of the fetched HTML page then each form will be interpreted and the relevant fields for each form will be displayed. Any cookies received during the request will also be logged here.
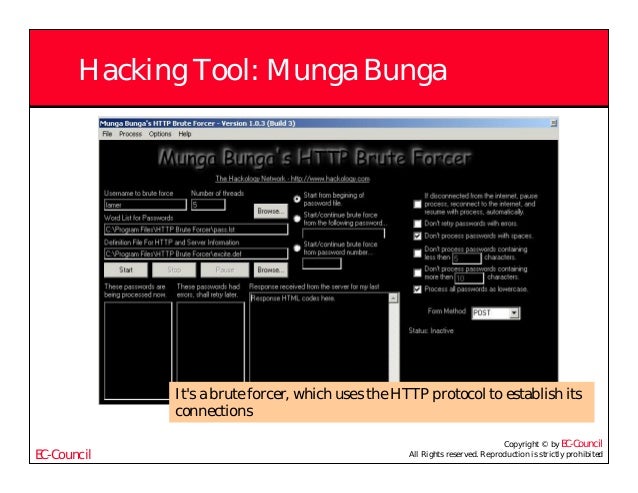
Brutus handles each authentication attempt as a series of stages, as each stage is completed the authentication attempt is progressed until either a positive or negative authentication result is returned at which point Brutus can either disconnect and retry or loop back to some stage within the authentication sequence. Munga Bunga’s HTTP Brute Forcer is a utility utilizing the HTTP protocol to brute force into any login mechanism/system that requires a username and password, on a web page (or HTML form).
To recap – A password usually only contains letters. In such a case the quantity of characters in a charset is 26 or 52, depending on usage of registers – both of them or just one. Some systems (Windows, for example) don’t make any difference between lower-case and uppercase letters. With an 8-characters’ long password the difference would amount to 256 times, which is really significant. Brute force method can sometimes be very effective when it is combined with the functionality of the program. Munga Bunga is a tool which can be used for breaking into emails, affiliate programs, web sites, any web based accounts, launching DoS attacks, flooding emails, flooding forms, flooding databases and much more; though DoS attacks and flooding activity are not supported or documented in the documentation.
Apart from this, the attacker can write definition files. These are files ending in the.def extension, and contain information about a particular server, and the data to submit to it. They are used to extend the power and capability of the program, based on the user’s own definitions. The software comes bundled with some definition. Passlist is a character based password generator that implements a small routine which automates the task of creating a “passlist.txt” file for any brute force tool. The program does not require much information to work.
The tool allows the user to specify the generation of passwords based on any given parameter. For instance, if the user knows that the target system’s password starts with a particular phrase or number, he can specify this.
This makes the list more meaningful to the user and easier for the brute forcer. He can also specify the length required such as the maximum number of random characters per password, apart from the maximum number of random.
Munga Bunga`s Http Brute Force S Review
Munga Bunga's HTTP Brute Forcer is a utility utilizing the HTTP protocol to brute forceinto any login mechanism/system that requires a username and password, on a web page (or HTML form).In simple terms, if you can access an account on the web, by entering a username and password(or more), then you can brute force into that account, using this utility.Brute Forcing is the process of trying various passwords from a dictionary file (automatically),for a given username, until the password matches the username.This method can sometimes be very effective. When you combine the power of brute forcing, withthe functionality of the program, then you end up with a tool which can be used for breaking into emails, affiliate programs,web sites, (any web based accounts), launching DoS attacks, flood emails, flood forms, flood databases and all that your imaginationcan extend too! However, you should note that DoS attacks and flooding activity is not supported or documented in the documentation.The utility only supports Brute Forcing (documentation wise). It can be used for other purposes, if you know how to writethe definitions to drive those forces.Definition Files are files ending in the.def extension, and contain information about a particularserver, and the data to submit to it. Definition files are typically written by users. They are used to extend the power andcapability of the program, based on your own definitions. However, the software comes bundled with some definition files.Updated.
Some Unique FeaturesA listing of some unique and nice features of this utility. AccessDiver is a software which can detect security failures on your web pages. It has multipleefficient tools which will verify the robustness of your accounts and directories accurately. So, you will know if your customers,your users and yourself can safely use your web site. Contains fast security that uses up to 100 bots to do itsanalysis. Detects directory failures by comparing hundreds of knownproblems to your site. AccessDiver is fully proxy compliant and has a proxy analyzer(speed / anonymity) and a proxy hunter built-in.
A built-in word leecher helps you increase the size of yourdictionaries to expand and reinforce your analysis. A powerful task automizer manages your jobs transparently. You can tackleunlrelated tasks while Accessdiver is working, saving you time. An on-the-fly word manipulator lets you increase the strengthof your dictionaries easily when doing your analyzis.
A PING tester is included to tell you the efficiency of yoursite and the efficiency of an Internet address you would like to access. A DNS resolver lets you look up the host name of an IP address and reversethe process to learn an unknown host name. A feature called 'HTTP debugger' helps your understandingof how actual HTTP protocol works. Untold stories minecraft maps.
It opens up the process so you see what really happens during a connection problem. A WHOIS gadget lets you retrieve owner information of a domainname (in case you would like to buy the domain or contact the actual owner). An update notifier automatically tells you when a new versionof AccessDiver is available.
A leeching system allows you to collect new proxies to makebetter proxy lists. A proxy Hunting system allows you to get even more proxiesby scanning IP regions. A file splitting and file merging system allows you to mixup files, orcut them in mutiple parts. That's good to handle wordlists or proxylists.requirements -. A PC compatible machine.
Windows 9x,Me,2000,XP,2003. 7 MB ofspace on your disk. 192MB of memory (RAM). Pentium200 or higher. Screenresolution: 800x600.